Personally identifiable information consists of various data, ranging from names and email addresses to more subtle details like IP addresses and biometric records. It’s the digital fingerprint that distinguishes one user from another in the virtual realm.
Protecting sensitive information like PII is essential. When you respect this kind of information, you build the cornerstone of trust with your audience and ensure compliance with legal requirements.
Whether you’re new to the online scene or a pro, this guide will equip you with the knowledge about PII. I’ll show you why this information matters for your business and give you simple steps to keep it safe.
- Personally identifiable information includes a wide range of data, from names and email addresses to less obvious details like IP addresses and biometric records.
- Sensitive PII includes data that can lead to identity theft, financial fraud, or personal safety concerns, such as social security numbers and medical records.
- To prevent illegal access to information relating to an identified individual, implement data encryption, access control, regular security audits, employee training, and strong password policies.
Table of Contents
PRO TIP: Take the hassle of writing your own privacy policy away with our privacy policy generator trusted by over 200,000 businesses. It’ll save you hours of work and possible costly legal mistakes.
What Is Personally Identifiable Information (PII)?
Personally identifiable information, commonly referred to as PII, is the kind of information that uniquely defines an individual’s online identity. It includes a wide array of personal data, such as full names, email addresses, phone numbers, home addresses, and social security numbers.
However, PII isn’t confined to the obvious; it also includes subtler details like IP addresses, biometric records, and even online usernames.
Respecting this kind of information is not only a responsible practice but also a fundamental requirement for maintaining trust with your audience and ensuring compliance with legal regulations. It’s about protecting your customers’ digital identities and creating a secure online environment.
PRO TIP: Understanding the depth and breadth of PII is key for online business owners. It helps you protect what matters most – your customers’ trust, your most valuable asset.
Differences Between Sensitive vs Non-Sensitive PII
PII can be sensitive or non-sensitive. Sensitive PII refers to data that can lead to identity theft or financial fraud, such as social security numbers and medical records. Non-sensitive PII, like names and email addresses, poses fewer risks if exposed.
Knowing the distinction between these types of data is important, as it guides how you handle and protect different types of information if malicious parties try to access PII of either kind.
Let us take a closer look at the contrast between sensitive and non-sensitive PII and what makes some data more delicate than others and better secure your online presence.
Sensitive PII
Sensitive PII only refers to information that can be exploited for malicious purposes, such as identity theft, financial fraud, or personal safety concerns. Misuse or exposure of sensitive data could lead to significant harm or privacy breaches.
The kinds of data that are considered sensitive include social security numbers (SSNs), financial account information, medical records, biometric data, passwords, and security questions.
By understanding what falls into this category, you can take the necessary steps to maintain digital security.
Non-sensitive PII
Non-sensitive PII may refer to details that, if exposed, typically pose fewer risks compared to their sensitive counterparts. While this information is still linkable to an individual, it’s less likely to result in data breaches and cyberattacks if it falls into the wrong hands.
Some examples of non-sensitive personal information are names, email addresses, phone numbers, mailing addresses, and usernames.
When you know this distinction, you can effectively manage customer data, personalize experiences, and maintain privacy within ethical boundaries.
Even non-sensitive personal information, when mishandled, can damage customer trust. Treat all customer information and non-personal data with care to avoid privacy-related issues and maintain your reputation.
Are PII and Personal Information the Same?
No, PII and personal information are not the same. They share similarities, but there are key differences between the two that matter in the world of data privacy and security.
PII is a subset of personal information that focuses on data with clear identification potential. It refers to specific data elements that can be used to identify or distinguish an individual. Examples include names, social security numbers, and biometric records.
On the other hand, personal information is a broader category that includes any information or data related to an individual, whether or not it can directly identify them. It includes things like hobbies, preferences, or general demographics.
While personal information is valuable, it may not carry the same level of risk as PII when exposed.
PRO TIP: When handling PII and personal information, classify and prioritize your data protection efforts based on the sensitivity and potential risks associated with each type.
Types and Examples of PII
PII has several categories, each containing distinct data elements. This personal data includes identifying information, contact information, financial data, health and medical records, biometric data, and online credentials.
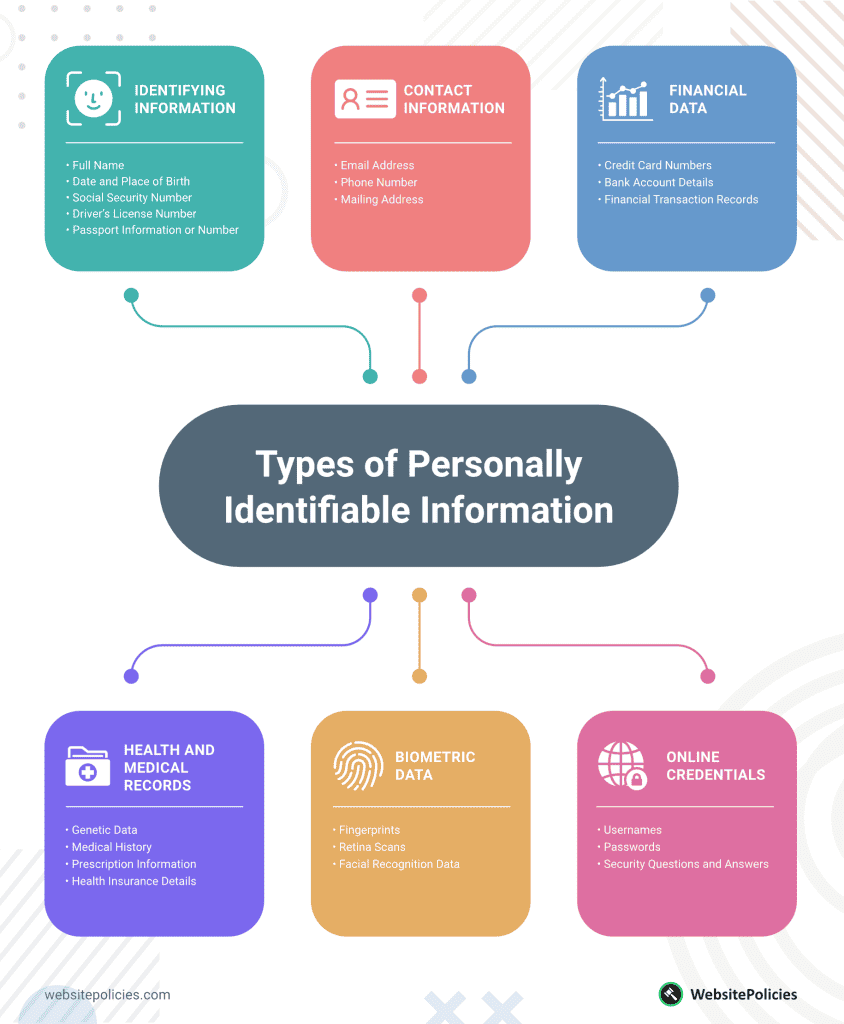
Identifying Information
Identifying information refers to data that directly associates a specific individual with their digital presence.
Often shared publicly, this available information is commonly the first target for identity theft. It also plays a major role in personalizing customer interactions.
Examples include:
- Full Name
- Date and Place of Birth
- Social Security Number
- Driver’s License Number
- Passport Information or Number
Contact Information
Contact information includes details necessary for communication but can also be exploited if mishandled. These details are important in online communication and should be protected to avoid spam or phishing attempts.
Examples include:
- Email Address
- Phone Number
- Mailing Address
Financial Data
Financial data comprises information tied to your economic identity. Securing this PII data is important to prevent fraud, unauthorized access, and monetary losses.
Examples include:
- Credit Card Numbers
- Bank Account Details
- Financial Information or Transaction Records
Health and Medical Records
Health and medical records pertain to your physical well-being or health information. Protecting this category of personal or identifying information safeguards privacy and prevents medical identity theft (think the Health Insurance Portability and Accountability Act of 1996, or HIPAA).
Examples include:
- Genetic Data
- Medical History
- Prescription Information
- Health Insurance Details
Biometric Data
Biometric data is unique physical or behavioral traits that are linked or linkable to a specific individual. This data can be used to distinguish or trace an individual and once compromised, it can have serious implications for security.
Examples include:
- Fingerprints
- Retina Scans
- Facial Recognition Data
Online Credentials
Data is considered online credentials if it is necessary for accessing digital accounts.
Examples include:
- Usernames
- Passwords
- Security Questions and Answers
Examples of Non-PII
Non-PII, which consists of information less likely to result in significant harm or privacy breaches, includes general demographics, preferences and interests, behavioral data, location information, and device and technical data which may become PII you’re not as focused on defending.
General Demographics
General demographics are related to characteristics linked to an identified or identifiable natural person. These are details or data that can be used to personalize content and services without exposing sensitive information.
Examples include:
- Age
- Gender
- Marital Status
Preferences and Interests
Preferences and interests involve data related to your likes and dislikes. This information aids in tailoring advertisements and recommendations without compromising your privacy.
Examples include:
- Favorite Color
- Hobbies
- Music Taste
Behavioral Data
Behavioral data tracks your online actions and interactions without revealing personal identification or the identity of an individual. This user data helps you improve user experiences while ensuring information security.
Examples include:
- Website Clicks
- Search Queries
- Purchase History
Location Information
Location data sets are defined as information related to your geographic data, providing insights without revealing specific addresses. These are used for services like local weather forecasts and regional recommendations.
Examples include:
- GPS Coordinates
- Zip Codes
- City or Region
Device and Technical Data
Device and technical data encompass information about your devices and online activities. In this age of information technology, this category largely helps in optimizing website performance and user experience.
Examples include:
- Device Type
- Browser History
- App Usage
ALSO READ: Customizable Privacy Policy Template
Data Privacy Laws That Protect PII
Several countries have enacted stringent data privacy laws or data protection laws to safeguard personally identifiable information. The goal is to ensure PII’s responsible handling and protection, offering individuals greater control over their personal information.
Below are a few countries and their data privacy regulations, highlighting how they define and protect PII.
United States
Definition and Protection of PII: In the U.S., PII is broadly defined to include various personal data like names, addresses, and social security numbers. The Privacy Shield Framework, the Privacy Act of 1974, and the California Consumer Privacy Act (CCPA) are significant legislations addressing data privacy.
Protection Highlights: The Privacy Shield governs transatlantic data transfers, ensuring that EU citizens’ PII is protected when transferred to the U.S. On the other hand, the CCPA grants California residents the right to know what PII is collected and the right to opt out of its sale.
European Union
Definition and Protection of PII: European Union’s General Data Protection Regulation (GDPR) considers PII as any information that can directly or indirectly distinguish or trace an individual’s identity. GDPR applies not only to EU citizens’ data but also to any organization handling such data.
Protection Highlights: GDPR mandates obtaining explicit consent for data processing, stringent breach notification requirements, and the right to be forgotten (data erasure). It imposes heavy fines for non-compliance, ensuring organizations like yours take PII protection seriously when they write their privacy policy.
Canada
Definition and Protection of PII: Under the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada, what qualifies as PII is any information about an identifiable individual. PIPEDA applies to organizations handling PII for commercial purposes.
Protection Highlights: PIPEDA requires obtaining consent for data collection, limits data sharing, and mandates data security measures. It offers individuals access to their PII and the ability to challenge its accuracy.
Australia
Definition and Protection of PII: According to Australia’s Privacy Act 1988, PII is personal data or information that can be used to identify an individual or trace an individual’s identity. The act applies to most Australian government agencies, businesses, and not-for-profit organizations.
Protection Highlights: This act regulates the collection, use, and disclosure of PII and mandates the adoption of suitable data security measures. It grants individuals the right to access their data and request corrections.
United Kingdom
Definition and Protection of PII: With the United Kingdom’s Data Protection Act 2018, data is considered PII if it relates to an identified or identifiable living individual. It closely aligns with the European Union’s GDPR.
Protection Highlights: The Data Protection Act 2018 regulates the processing of PII and sets stringent standards for data protection. It emphasizes data subjects’ rights, including access, correction, and erasure of their personal data.
Brazil
Definition and Protection of PII: The LGPD (Lei Geral de Proteção de Dados) in Brazil defines PII as any information that is linked to an identified or identifiable individual. The law is similar in structure to GDPR.
Protection Highlights: LGPD regulates the processing of PII, mandates data breach notifications, and grants data subjects rights to access and erase their personal data. It imposes fines for non-compliance to ensure robust PII protection.
PRO TIP: Regardless of the laws, it’s always a good idea to exercise good privacy and security practices and protect your customers’ data.
Common Ways Used to Steal PII
Protecting personally identifiable information is necessary because such information can be targeted by various malicious actors. Here are some common methods that can be used to obtain someone’s PII. Being aware of them will hopefully help you protect your data better.
- Phishing Attacks: Cybercriminals send deceptive emails or messages pretending to be from trusted sources, tricking recipients into revealing PII like login credentials or credit card numbers.
- Data Breaches: Hackers can access or infiltrate databases or systems to get their hands on PII stored by organizations, which results in large amounts of personal data being exposed. It’s important that you brush up on data and security breaches as well as take preventative measures to keep personal data safe and reduce the number of data breaches your organization experiences.
- Malware and Ransomware: Malicious software infects a device, which then gives hackers unauthorized access to PII and allows them to encrypt files until a ransom is paid.
- Physical Theft: PII can be stolen through the physical access or theft of physical documents, relevant data, wallets, laptops, or mobile devices.
- Dumpster Diving: Attackers sift through discarded documents or trash to find PII on physical records.
- Man-in-the-Middle (MitM) Attacks: In MitM attacks, hackers intercept communication between two parties without their knowledge. This can occur in public Wi-Fi networks or compromised routers, and it allows attackers to capture PII, such as login credentials, credit card numbers, or sensitive messages.
- Keyloggers: Keyloggers are malware or hardware devices that record keystrokes on a computer or mobile device. They capture login credentials, credit card numbers, and other sensitive information as users type.
- SIM Swapping: Attackers persuade mobile service providers to transfer a victim’s phone number to a new SIM card under their control. This enables them to intercept SMS-based two-factor authentication codes and gain access to accounts.
- Eavesdropping and Wiretapping: Sophisticated attackers may eavesdrop on phone calls or communications through wiretapping. They can gain access to sensitive conversations or information being transmitted.
- Insider Threats: Insiders with authorized access to systems and databases may misuse their privileges to steal sensitive personal data. This can be employees, contractors, or anyone with legitimate access.
Potential Risks of PII Being Stolen
One of the most immediate and alarming risks associated with PII theft is identity theft. A significant breach can lead to a substantial erosion of trust among your user base. I’ve consulted with various companies post-data breaches, and the common thread is always the challenge of regaining customer confidence.
When users entrust you with their data, they expect you to guard it with the utmost care. A breach can signal to them that their trust was misplaced. And in the age of social media and instant news, word spreads fast. A single incident can tarnish your brand’s image, making it difficult to attract new customers or retain existing ones.
Then there’s the legal landscape to consider. Many countries have implemented stringent data protection regulations as I mentioned above. On top of that, individual states have their own set of regulations.
Non-compliance or breaches can result in substantial fines, not to mention the cost of litigation if affected parties decide to sue. I’ve seen businesses grapple with these consequences, and it’s never a pretty sight.
Finally, the aftermath of a PII breach isn’t just about addressing the immediate fallout.
There’s a long-term impact of PII being stolen that can divert your resources from growth and innovation. Increased scrutiny from regulators, the need for more robust security measures, and public relations campaigns to restore reputation – these are all resource-intensive endeavors.
How Can You Protect Your Customers’ PII?
First and foremost, encryption is your best friend. Whether it’s data in transit or at rest, encryption ensures that even if data is intercepted, it remains unreadable to unauthorized parties. I’ve seen businesses overlook this basic step, only to regret it later.
Regularly updating the software and products is another critical measure. Cybercriminals often exploit vulnerabilities in outdated software. By keeping all systems up-to-date, you reduce the risk of such attacks.
PRO TIP: Remember, it’s not just about updating your website’s platform but also any plugins or third-party tools you use.
Multi-factor authentication (MFA) adds an extra layer of security. By requiring users to provide two or more verification methods, you significantly reduce the chances of unauthorized access. I always recommend this to businesses, especially for their administrative portals.
Training is often underestimated. Ensure that your team understands the importance of data privacy and knows how to recognize potential threats. A well-informed team can be your first line of defense against phishing attacks or other deceptive tactics.
Lastly, create a comprehensive privacy policy and consider regular security audits. Hiring external experts to assess your security measures can provide valuable insights. They can spot potential weaknesses you might have missed and recommend solutions. In my experience, a fresh pair of eyes often catches what’s hidden in plain sight.
Frequently Asked Questions
What is personally identifiable information (PII)?
PII refers to information that uniquely defines an individual’s online identity, including names, email addresses, IP addresses, biometric records, and more.
What’s the difference between sensitive and non-sensitive PII?
Sensitive PII can lead to identity theft or financial fraud, like social security numbers. Non-sensitive PII, like names, poses fewer risks if exposed.
Are PII and personal information the same?
No, PII focuses on identifiable data like SSNs, while personal information is broader, covering hobbies, preferences, and demographics.
What are the potential risks of PII being stolen?
Risks include identity theft, financial loss, damaged reputation, legal consequences, and emotional distress for victims.
How can businesses protect customers’ PII?
Protect PII through encryption, access control, security audits, employee training, strong passwords, and clear privacy policies.